- When viruses invade your computer system, DON'T raise your hands in fear! Call the rock stars who will get them out of there!
- 1-888-576-2578
Thousands of Mac Programs Potentially Vulnerable. Are you Affected?

Trend Micro Emergency Update
January 26, 2016
Ethical Hacking Presentation
February 17, 2016
Using a Mac-operated computer provides you with several advantages. People consider buying Mac-operated devices for the high end performances, classy finish and relatively higher security features.
However, as per one of the latest threats reveals, Mac users have a significant potential to be vulnerable from thousands of third party apps pertaining to the Sparkle framework.
What is Sparkle?
Most Mac users won’t immediately recognize Sparkle and so may quickly dismiss it.
However, before you do so, Sparkle is a framework which is widely used within Mac OSX by thousands of app developers.
This is open source (free to use) software developed by Sparkle Project for app developers to provide manual and automated updates in the background for widely used third party software like µTtorrent, Camtasia Duet Display and Sketch.
What is the risk?
The main risk of this particular loophole is that it makes you open to MitM or MITMA attacks (man in the middle attacks).
When you are under a MitM attack, your communications via the Internet can be exposed to someone else in the middle without your knowledge.
When your Mac device starts to update any software that uses Sparkle, since your communication with the update server is exposed to a third person you do not know, they can insert harmful code and gain full control of your computer system putting your privacy at major risk.
Sparkle Updater Framework Video
This 28 second video show how it is possible, in terms of misconfiguration provided with the Sparkle Updater framework.
What are the apps under attack?
If you are currently running one or more of the below mentioned apps in your Mac, you might be under a potential risk of being attacked.
- Acorn, Adium, Bittorrent Sync, Carbon Copy Cloner, Cinch, Colloquy, Evernote, Fantastical, Fitbit, Connect, Flux, Handbrake, iTerm, Karabiner, Sequel Pro, Sidestep, Slack, Transmission, Twitterrific, Vienna, Vivaldi, VLC, WebKit Nightly and Wine.
Applications using Sparkle is a user generated listed of those apps that use Sparkle to perform software updates.
IMPORTANT: Not all apps are vulnerable. Some apps were originally programmed with security in mind. Some apps developers have already updated their software effectively removing this vulnerability.
How do I know if I’m using Sparkle and if so, what version are each app using?
Each app is separately affected by this vulnerability. Here are the steps to determine which of your apps are using Sparkle as well as what version of Sparkle (code credit goes to HipsterPixel.co):
- Open the terminal (open applications folder, utilities folder, click the terminal application)
- Copy the following code into the box and run the command:
find /Applications -name Sparkle.framework | sed 's,/Applications/\(.*\)\.app/Resources/Info.*,\1,'|while read fname; do
appname=$(echo $fname | sed -e 's/\/Contents\/Frameworks\/Sparkle\.framework//g' | sed -e 's/\/Applications\///g')
version="$(defaults read "$fname/Resources/Info" CFBundleShortVersionString)"
echo "$appname => $version"
done
You will have a response similar to the following:
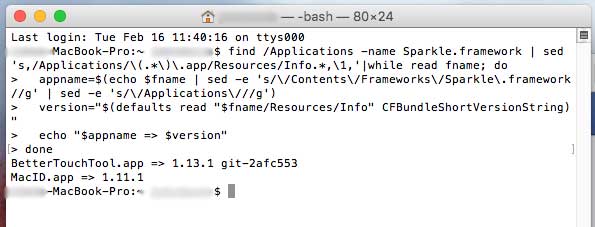
(computer name was blurred for privacy of customer)
Notice this customer as two apps that use Sparkle. The BetterTouchTool is using Sparkle version 1.13.1 while the MacID is using 1.11.1. The MacID in this example is potentially vulnerable until it is updated to 1.13.1 or more recent.
Is there any way to be protected?
After seeing the problem, the Sparkle Project developers are very passionate about their work and have taken measures to fix this problem on their end with Sparkle version 1.13.1+.
Their newest version claims to have fixed all the bugs, but installing the patch may not be the easiest task.
From the app developers’ point of view, the app developer needs to download the latest version of Sparkle and make their app 100% compatible with the new Sparkle framework.
From the users’ perspective, concerning the protection, you need to download the latest version of your apps and use it.
- If you’ve manually downloaded Sparkle, update to the latest version of Sparkle.
- Check with your app developer to ensure they have updated to the latest version of Sparkle.
- Disable automated updates of any apps that use old versions of Sparkle (prior to 1.13.1). Unfortunately, some apps don’t include this functionality. Check with the app vendor.
- Until all the apps you use are compatible with the latest Sparkle version, you are advised to use a Virtual Private Network (VPN) to do your online communications. VPNs will protect against many MiTM vulnerabilities if set up properly, but not all of them.
- Also, you should remember to avoid public and unsecured Wi-Fi networks to browse the Internet until you get the updated apps.
By any chance, if you are prompted to perform an update, it is better to avoid it and directly download the latest version from the official website. It will make sure that you end-up with the expected result other than getting misdirected.



