- When viruses invade your computer system, DON'T raise your hands in fear! Call the rock stars who will get them out of there!
- 1-888-576-2578
Roger Whittaker
July 21, 2016
Most Netflix users will try their best to avoid an interruption of their Netflix service. Avoid this scammer trick and keep Netflix safely streaming your shows. […]
April 20, 2016
Uninstall Apple QuickTime which contains two known vulnerabilities that can allow an attacker to execute their own deceptive code on your computer. Since Apple ended support […]
April 20, 2016
Stephen Oakes, Special Agent assigned to the FBI Louisville Division’s Cyber Squad, presented at a recent information technology meeting attended by local IT professionals. Oakes has […]
March 4, 2016
Encryption viruses cause panic in all those stricken by it from homes with one computer to a business with 100’s of computers. Thankfully there is some […]
February 17, 2016
Robert Parsons, President of Automated Office Solutions Inc. presented at a recent information technology meeting attended by local IT professionals. Parsons (“The Other Bob Parsons”) is […]
February 16, 2016
Using a Mac-operated computer provides you with several advantages. People consider buying Mac-operated devices for the high end performances, classy finish and relatively higher security features. However, […]
January 26, 2016
If you have Trend Micro anti-virus, make sure you immediately update to the latest version. Trend Micro version 10.0.1186 leaks stored passwords as well as has […]
January 25, 2016
Online advertising is big business. Virus writers attack ads that are delivered to popular and safe websites, replacing good ads with malware, viruses and other infections. […]
January 21, 2016
Should I format my hard drive and reinstall Windows? Good question, let’s explore this option. Before formatting and reinstalling Windows or getting a new computer: Document your […]
January 21, 2016
Here’s another backup solution that might work great for you. It includes the hardware and software for a one purchase backup solution. How does it work? […]
January 21, 2016
If you already have a USB external hard drive, consider using software to backup to your external hard drive. Optionally, you can purchase an external USB […]
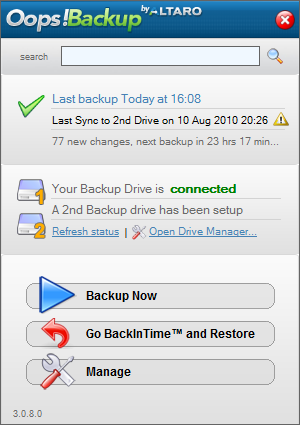
January 21, 2016
Here’s a backup solution that might work great for you. It includes the hardware and software for a one purchase backup solution. How does it work? […]
January 16, 2016
The New Business Offers an Effective Virus Removal Plan for Windows The founder of Rock Star Virus Removal, a computer virus removal service, is pleased to […]
January 15, 2016
How Rock Star Virus Removal Helps Victims of Tech Support Scams • Everyone has experienced the frustration of a computer that moves slow as molasses. • […]
January 14, 2016
Keeping Your Business Safe From Cyber Attacks Heading in to the store one day you hear on the radio about the newest Trojan Horse Virus that […]